Cyber-attacks continue to be a real issue for UK businesses. The tactics used by cyber criminals are constantly changing, with more elaborate schemes being put into play to dupe staff into revealing sensitive information and paying over money under false pretences. We have particularly seen a significant increase in targeted fishing scams, so here, we’ll take a closer look at what this tactic looks like, as well as practical ways to overcome this threat within your business.
Targeted phishing scams
Cyber criminals have become well versed in how to create a convincing targeted attack on a business. Simple research on a business, perhaps through staff profiles or social media accounts, will reveal the best people to target. These are usually management staff with access to sensitive information or staff closely linked with business operations and finance, such as accounts teams and CFOs.
Once this information is obtained, cyber criminals can create surprisingly convincing emails scams that target a particular individual. They may pose as another member of staff or a supplier of the business seeking payment. If they already have access to a business’s network, they may also watch email correspondence, waiting for the right moment to intercept an invoice and redirect the payment.
Here’s a convincing example of this payment request phishing tactic in play.
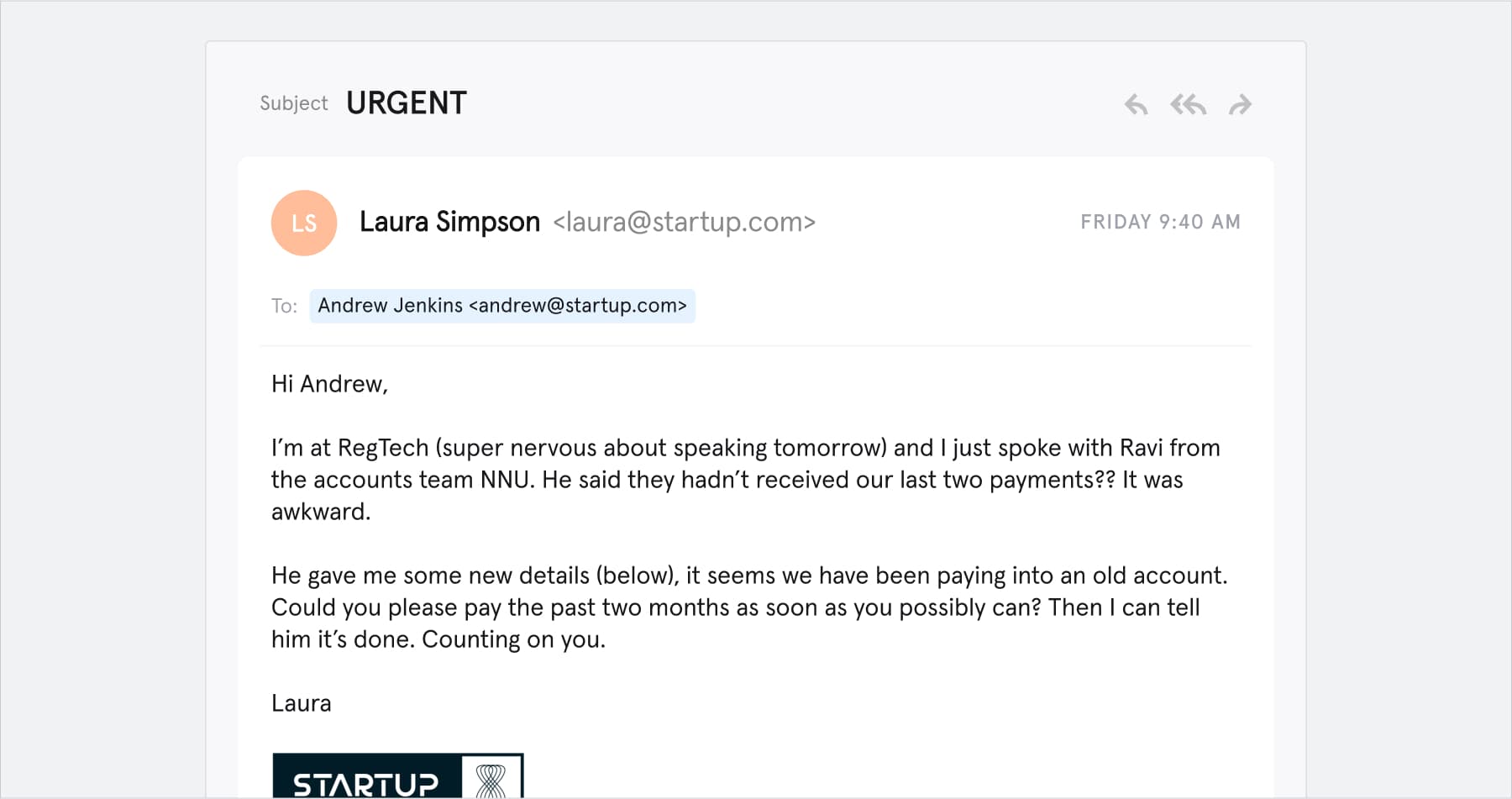
This type of communication could also be used to convince the recipient to click a link, which could, for example, download malware onto the business network, allowing cyber criminals to gain access into a business’s systems and hold digital assets to ransom.
How can businesses protect against targeted cyber attacks?
There are a number of practical ways in which businesses can mitigate risks to this increasing threat from phishing scams. These include:
Training
With 85% of all breaches coming from staff responding to, or clicking on fictitious emails; staff need to be aware of the latest tactics and potential red flags that cyber criminals are using and learn how best to recognise them. Building in time to question the emails you are receiving is crucial, but easier said than done if staff with the pace of work these days. Organising a business’s operations and culture to support staff in their ability to recognise these cyber-attacks is of paramount importance.
Passwords
According to recent research by Cyber Edge, the majority of data breaches – some 80% – were due to poor password practices leading to account takeovers. Two-step verification (2SV) has been effective in protecting systems and should be adopted across an organisation, including with email logins. However, individual passwords still tend to be of poor quality.
The general rules when it comes to passwords are:
- To never stick with a default password or code,
- To never use personal information (dates, family or pet names etc.) or obvious passwords,
- And to never duplicate the password across logins, including adding extra digits or characters when updating a password.
The most effective passwords, according to National Cyber Security Centre, will contain a string of three random words, or will be compiled (and stored) by a password manager. A novel way to create such a password is using the location app What3Words. For example, if you choose Nelson’s Column in Trafalgar Square you will get the three random words MileCrazyShade, or the entrance to Canary Wharf tube will produce SlotPipesAnimal. The more random, the better!
Checking if your credentials are on the dark web
There are several methods that cyber criminals will use to get hold of passwords, including phishing, malware, social engineering and exploiting vulnerabilities. But they also use the dark web to buy this information.
This data will have been gathered from an initial breach, which is then sold on the dark web, either individually or in larger data sets, to other hackers, who then attack the business again.
This is where dark web monitoring can provide an essential layer of security when incorporated into your overall cyber security strategy. A dark web scan can be carried out by an IT professional on an ongoing basis to keep your systems secure. You can also spot check an email address’s exposure on the dark web using a service such as SpyCoud.
Ongoing cyber security protection
It’s important for businesses to keep on top of these constantly changing cyber threats. Unfortunately, no one solution can achieve all of this. Rather, businesses need to adopt a holistic approach to their cyber security that will involve their systems, staff, processes and IT service provider.
Find out more
If you would like to know more about cyber security monitoring for your business, or any other aspect of this article contact Andrew Wayman at andrew.wayman@sdt.co.uk or call our office on +44 (0)1344 870062.

